Serious Intel CPU design flaw may require a Windows patch, but probably won't affect gaming performance
The fix can hurt performance in specific scenarios, but your frame rates will likely stay high.

A report on LWN, a Linux kernel development site (sub required), details of a hardware bug in modern Intel CPUs that allows an attacker to access low-level kernel memory that is normally protected from higher level (programs and user) access. As reported on The Register, this bug could have big consequences, requiring OS kernel patches on Windows, Linux, and OS X. Those fixes could actually cause the affected CPUs to perform more slowly, but don't panic: your gaming PC is unlikely going to see a dramatic change as a result.
This is complicated stuff, so I'll try to break it down. The method of attack revolves around identifying virtual memory pages in specific sequences that reveal locations in memory where protected kernel space resides. The bug is a hardware bug, so there's no easy fix except to wait for Intel to implement a fix in its next generation of CPUs. The flaw affects multiple generations of Intel CPUs.
The expected short term solution will come from OSes: operating systems can apply what's called a kernel Page Table Isolation (PTI) that cloaks kernel memory addresses. The caveat is that the fix will force the CPU to constantly flush its caches that hold its TLBs, or translation look-aside buffers, which are essentially caches that allow the CPU to quickly access user memory.
In some instances, a performance hit of up to 30 percent or more can be seen, due to the CPU flushing caches, and having to go to slower main memory to access data. While the instances are currently regulated to I/O intensive applications and virtual machines, it does pose a potential situation for slowdown in a desktop environment.
Right now, there's no evidence that the kernel patches will impact a single-user system and it's unlikely going to pose any serious impact for gaming. According to this breakdown of the issue, it seems that the security-related hardware bug will impact large scale applications, such as cloud services. Amazon, Google, and Microsoft are already working on fixes.
We've reached out to Intel for more information and will report back if we receive further details.
Update: A post by Thomas Lendacky, a PMTS software engineer for AMD, on LKML.org explains that AMD CPUs are not impacted by the same bug. Lendacky says that the PTI patch should not be enabled on AMD CPUs, as its memory controller doesn't allow the same memory references that would allow for less privileged calls to access high-privileged data.
PC Gamer Newsletter
Sign up to get the best content of the week, and great gaming deals, as picked by the editors.
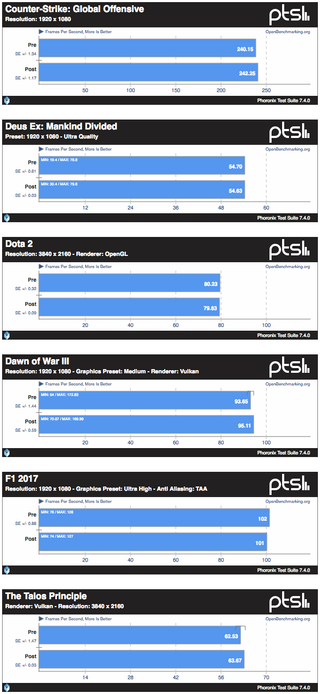
Phoronix (OpenBenchmark.org) has published several gaming benchmarks with Linux 4.5 using pre-patched and post-patched system, showing no impact on gaming-workloads. Benchmark was performed on an Intel Core i7 8700K using an AMD Radeon RX Vega 64:
Most Popular




