Parasitic malware tricks crypto scammers into doing the hard work for them
Hodl the phone, where did all my stolen crypto go?

In a world where scammers are rife, and seemingly obsessed with hacking innocent parties—like the Costa Rican healthcare system—in order to hold their data ransom for crypto capital, we almost got excited when we heard about malware that intercepted scammers before they could profit from their misdeeds. Unfortunately, it's not all good news.
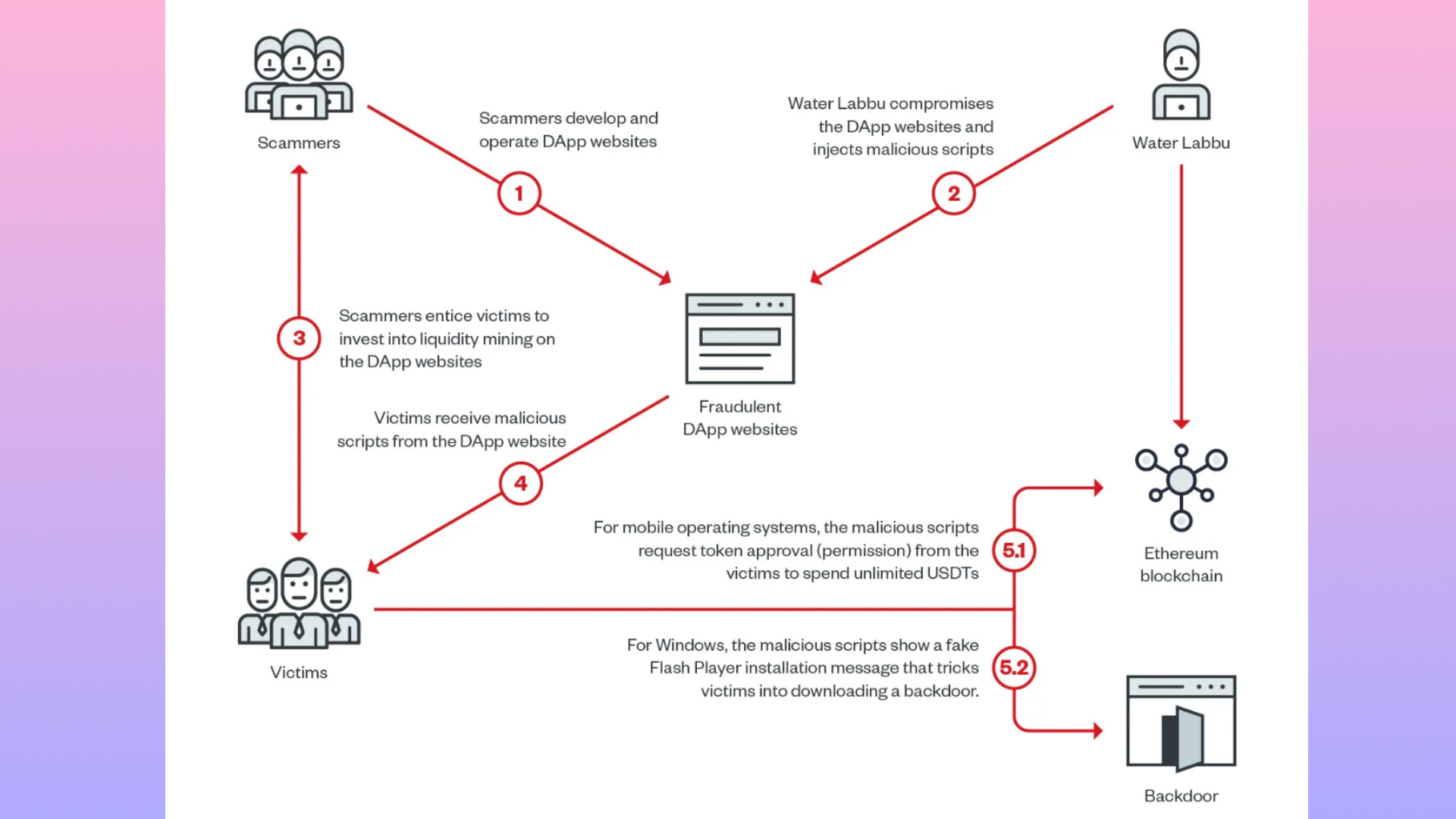
Trend Micro outlines in a recent post a parasitic threat actor the company just discovered. It's been named Water Labbu, potentially as a nod to a Mesopotamian lion-dragon-like mythological creature designed by the God Enlil to wipe out the nuisance that humanity had become. The rest of the Gods ended up cowering before it and he finally sent someone to slay the beast which took three years, three months, and a day to bleed out.
The more you know...
Water Labbu (the malicious actor, not the creature) had been targeting problematic cryptocurrency scam websites, piggybacking off the social engineering tactics many crypto scammers use, such as convincing people to hand over passwords, etc, in order to turn the tables on would-be scammers.
It would hide behind the guise of a decentralised application (DApp) and infect the crypto scammers' websites, waiting for a victim whose crypto wallet was overflowing to connect to the site. It then asks for permission from the original scammer to transfer an ungodly amount of USD Tether (USDT) from their target, making itself seem less threatening by hiding behind the DApp mask.
"If the victim loads the script from a mobile device using Android or iOS," the report notes, "it returns the first stage script with cryptocurrency-theft capabilities."
"If the victim loads the script from a desktop running Windows, it returns another script showing a fake Flash Player update message asking the victim to download a malicious executable file."
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.

Best CPU for gaming: The top chips from Intel and AMD
Best gaming motherboard: The right boards
Best graphics card: Your perfect pixel-pusher awaits
Best SSD for gaming: Get into the game ahead of the rest
If the scammer accepts the permissions without reading them properly, the script essentially allows Water Labbu to intercept the scammer in their wrongdoings, turning them into the victim and draining their wallet. So far, Trend Micro reports that over $300,000 has been stolen in this parasitic manner, from at least nine victims.
And while there's always a part of me that loves to hear of scammers getting their comeuppance, their original victims are still victims here. I've heard nothing about Water Labbu's stewards going all Robin Hood and paying the money back, at least not yet.
Until then I'm not even sure it's worthy of the epic Mesopotamian beast's name; less of a mighty, world-ending dragon that instils fear even in the Gods themselves, more like a crypto tapeworm.

Screw sports, Katie would rather watch Intel, AMD and Nvidia go at it. Having been obsessed with computers and graphics for three long decades, she took Game Art and Design up to Masters level at uni, and has been rambling about games, tech and science—rather sarcastically—for four years since. She can be found admiring technological advancements, scrambling for scintillating Raspberry Pi projects, preaching cybersecurity awareness, sighing over semiconductors, and gawping at the latest GPU upgrades. Right now she's waiting patiently for her chance to upload her consciousness into the cloud.

