Our Verdict
The YubiKey NEO and NEO-n are durable, easy-to-use security devices that can help save your digital bacon.
PC Gamer's got your back
Your passwords aren't strong enough
When it comes to contemporary security, the humble password (or passphrase) isn't enough to keep you safe. It seems like every day someone breaks into an organization's database and steals an array of passwords and user IDs. Even if organizations could keep their systems totally safe, some people still use low-tier passwords out of laziness.
One Key to Rule Them All: Secure 2FA with a slew of options like OATH-HOTP, HMAC-SHA1, and Yubico OTP; can securely store 2048-bit RSA keys; FIDO U2F compatible.
And In The Darkness Bind Them: Not all services offer U2F, OATH, or HMAC; small enough to lose easily.
It's for this reason that password managers are so handy, but even the password manager can be insecure due to its reliance on a password to secure it. Luckily, two-factor authentication (2FA) is beginning to become the norm. (If you haven't activated two-step verification for your Google account, stop what you're doing and activate it now.)
For those who want more than what Google Authenticator has to offer, there's Yubico's YubiKey. YubiKeys come in several models, and I got a chance to play with a YubiKey NEO and YubiKey NEO-n. Both of them are kick-ass pieces of security hardware.
The YubiKey NEO is an unassuming-looking USB device that you attach to a key-ring or lanyard. When inserted into your PC, the user only needs to touch the gold button on the YubiKey for it to work. (The button is capacitive, not a fingerprint reader.) The YubiKey NEO also supports NFC, so you can use the key with an Android device.
The NEO-n is a low-profile USB key that, when inserted, is nearly flush with the side of your laptop or USB port. To activate the NEO-n, you simply touch the exposed side of the device while it's inserted. The NEO-n does not have NFC capability.
Each YubiKey is unique, and will have to be paired with services separately. (If you have a NEO and a NEO-n, they will give different responses to whatever service is requesting input.) The devices also register as HID keyboards by default, so they will work without having to install any drivers. That's a big plus in my book.
Three functions in one key
The YubiKey NEO and NEO-n have three modes of use, and you can enable all of them at once with the newer firmware. (Older firmware only allowed the user to enable two at a time.) All YubiKeys (with the exception of the $18 blue Fido U2F Security Key model, which only has FIDO U2F support) ship with one-time password (OTP) mode enabled by default.
Services that use OTP authentication (like LastPass) make use of Yubico's cloud service to authenticate YubiKeys. In this mode, the YubiKey supplies a string of characters. The first few characters of the string is the YubiKey identifier and always remains the same. The rest of the string is a unique code made up of a cryptographic nonce. When the string is supplied to the service (like LastPass), the service checks it against the Yubico cloud to authenticate the string. If the service gets the okay from Yubico, access is granted. In this manner, the OTP mode basically serves as a second username and password, in which the password (nonce) for the YubiKey changes every time it's used.
The second mode that the NEO and NEO-n can use is chip card interface device mode, or CCID. In CCID mode, the NEO can store OpenPGP keys for use on different PCs. For those who use OpenPGP/GnuPG, this means that you won't have to carry around private and public key-files on a FAT32-formatted USB stick—though you should always keep a backup of your private key somewhere secure like a USB stick in a locked box. By extension, it also means that you won't have to move those keys to your PC. The only setback to this mode is that the YubiKey NEO (and NEO-n) only support 2048-bit RSA keys. If you have a 4096-bit key, you can get around this by creating 2048-bit signing, authentication, and encryption keys and moving those onto your YubiKey using GnuPG. (Note: The YubiKey 4 supports 4096-bit keys in CCID mode, but lacks NFC capability.)
The last mode is U2F, which makes use of the FIDO U2F standard. There are several services that make use of FIDO U2F, like Google and GitHub. However, at the time of writing, Mozilla's Firefox browser doesn't support FIDO U2F. (Native support of U2F in Firefox is being worked on, and there is an active bug in Bugzilla tracking the issue.) If you want to use U2F with web applications, you have to go with Chrome for now.

Other authentication methods
There are other features the YubiKey NEO can implement via one of its two "slots." Slot one comes pre-configured with Yubico's OTP. The first slot is activated by a quick tap on the YubiKey's button, while a long (three to four second) tap activates Slot 2. Using the YubiKey Personalization Tool, you can configure Slot 2 to to use a static password, OATH-HOTP, or a challenge-response using either the Yubico or HMAC-SHA1 algorithm.
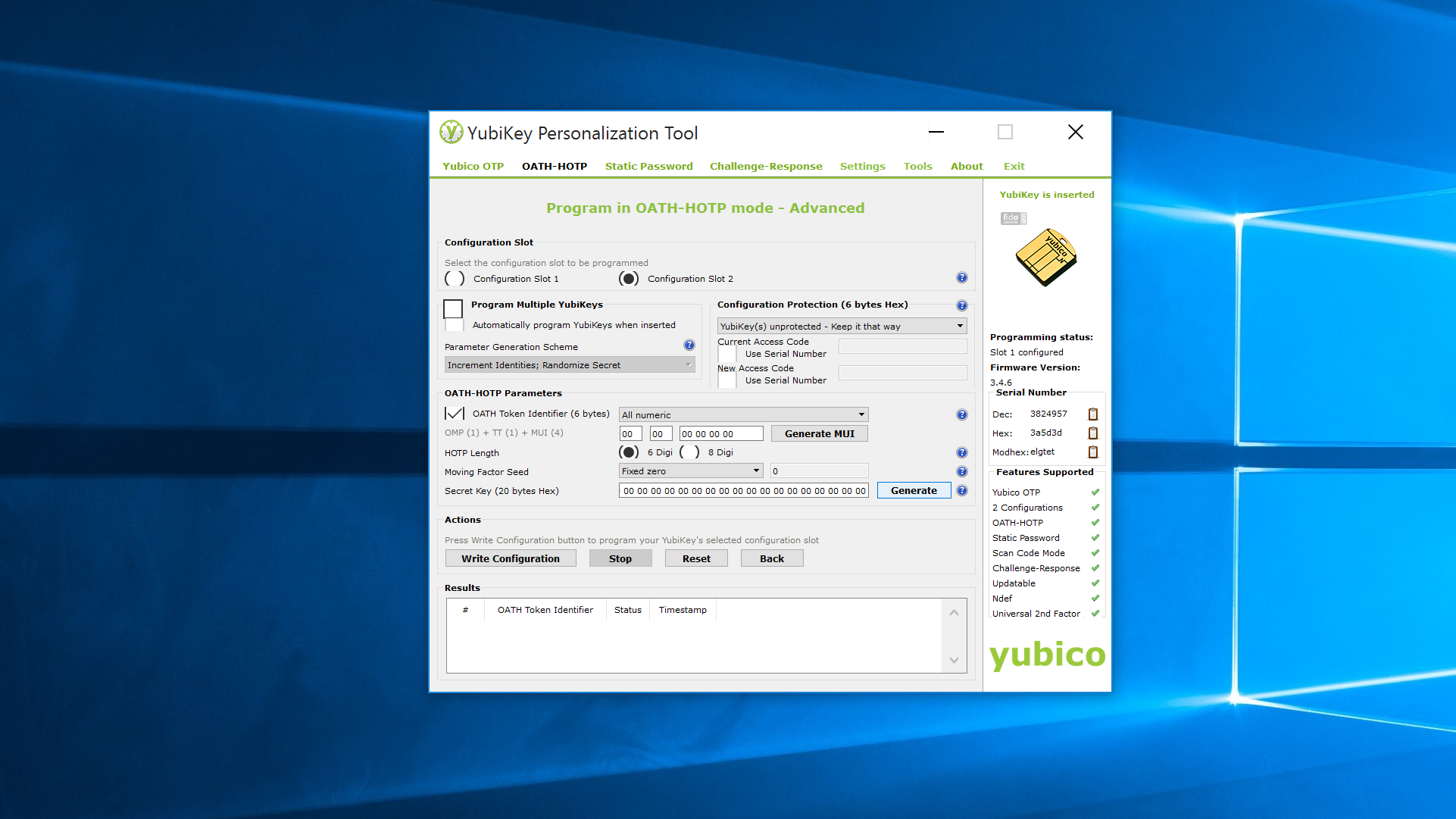
The static password is pretty straightforward, and has its uses in systems that don't support any other password method (like a BIOS password). The OATH-HOTP option generates a six to eight digit number, much like Google Authenticator or an SMS second-factor authentication method would. The HMAC-SHA1 feature allows for a system to challenge the YubiKey with a string that has to be combined with a shared secret and hashed before being sent back to the system. HMAC-SHA1 allows the YubiKey to be used for system logins with Yubico's login software for Windows, or with LUKS disk encryption on Linux.
Considering how small and simple the YubiKey is, that's an impressive array of security options that are available to the user. If you're still with me, let's go over one more really cool thing about the YubiKey NEO: NFC.
NFC and Yubico Authenticator
If you've ever used two-factor authentication, there's a good chance you've used Google Authenticator. Google Authenticator makes use of a shared secret, TOTP, and HMAC-SHA1 to generate one-time passwords that are generated on a clock cycle. It's reasonably secure, and lots of services use it because it's free, easy to use, and doesn't require the service to send SMS messages with one-time use codes.
But what if someone happens to unlock your phone? That 2FA isn't so secure. Yubico's Authenticator app requires the user to tap their YubiKey NEO to the back of their phone before codes are displayed. The codes that are displayed look and act just like Google's codes. The app can add any service that Google's Authenticator can, which makes the Yubico Authenticator a drop-in replacement for Google Authenticator.
Besides just using the YubiKey, the Yubico Authenticator allows you to lock the codes behind a password as well. This seems a little bit like overkill, since if someone has my phone, YubiKey, user name, and password, they're probably in a position where they can beat the Authenticator password out of me. Still, this feature offers security on top of security, and the truly paranoid can feel safe knowing that their one-time pass-codes are as secure as they can be.
Losing your keys
One bad thing about the YubiKey is that it's so small. The damned thing can be easy to lose if you're not careful. Even if attached to your key ring, the YubiKey is as easy to lose as your keys are. A couple of weeks ago I lost my keys on BART (Bay Area Rapid Transit), which meant I had to reset all of my YubiKey pairings.
Another thing that ticks me off is that I can't use the YubiKey NEO with some services that really should allow FIDO U2F or OATH-HOTP. PayPal (and other sites that use Symantec's VeriSign), won't work with any YubiKey except the YubiKey VIP, which you have to call in to order. Steam doesn't yet support U2F and sticks to its proprietary 2FA system. None of the financial organizations I use take advantage of U2F. But hey, you can bet your ass my Gmail is secure.
I was also a little worried at first about what could have happened if I had my PGP keys loaded on the YubiKey. Then I remembered that if you load subkeys and not your primary key, all you would have to do is revoke the subkeys.
The upside to having this thing on my key ring is that I always know where my keys are when I'm working on a PC: right next to me. Since I need the YubiKey to unlock my LastPass vault on a regular basis, my key ring is never far from my laptop or desktop.
Using 2FA and advanced security features online and on your PC can be a pain the ass sometimes, but the YubiKey makes it really easy once it's set up. The added confidence in knowing that only someone with your physical YubiKey can access your accounts gives peace of mind to using password managers and online services. For the consumer worried about security, you really can't get much better than using the YubiKey when it comes to securing online accounts. 2FA won't save you by itself (it can't defend against man-in-the-middle attacks, for example), but it will make you a harder target.
At $50, I can't recommend the YubiKey NEO highly enough. Though I got to review the YubiKey NEO-n, you can't get the NEON-n individually, as Yubico only sells them in batches of 500 or more. That's not a big deal, since the $50 YubiKey 4 Nano is pretty much the same thing as the NEO-n and can hold 4096-bit RSA keys to boot. However, if you don't need the NFC features or want the ability to store 4096-bit RSA OpenPGP keys, I'd recommend getting the cheaper YubiKey 4 for $40.
The YubiKey NEO and NEO-n are durable, easy-to-use security devices that can help save your digital bacon.



