Sens. Feinstein and Burr: I don't think you get it
You can't just legislate away encryption
Senators Feinstein and Burr, we have to talk about encryption.
It's not common practice for us to comment on policy here at PC Gamer Hardware (formerly maximumpc.com), though we do cover it in our news feeds. In my home state of California (that Sen. Feinstein represents), encryption has run up against the needs of law enforcement. This conflict over privacy and security has recently become a critically important issue to people across the U.S. and abroad.
Senators, you both recently co-sponsored a bill called the Compliance with Court Orders Act of 2016, attacking encryption in a way that would endanger personal privacy, the economy, and national security. I don’t question that you proposed this bill with the best of intentions, but it appears you don’t understand the technology you’re trying to legislate. Senators, this bill will lead to disaster if allowed to come to fruition.
The bill, as I read it in early April, did nothing to protect the American people, and succeeded only at putting everyone’s security at risk. You don’t need a PhD in mathematics or cryptography to understand the basics of encryption and its value in modern society, or why this bill endangers the banking system, critical infrastructure, and the personal information of everyone with an electronic footprint. In today's world, that class of people is growing ever rapidly, whether a person chooses to use the internet or not.
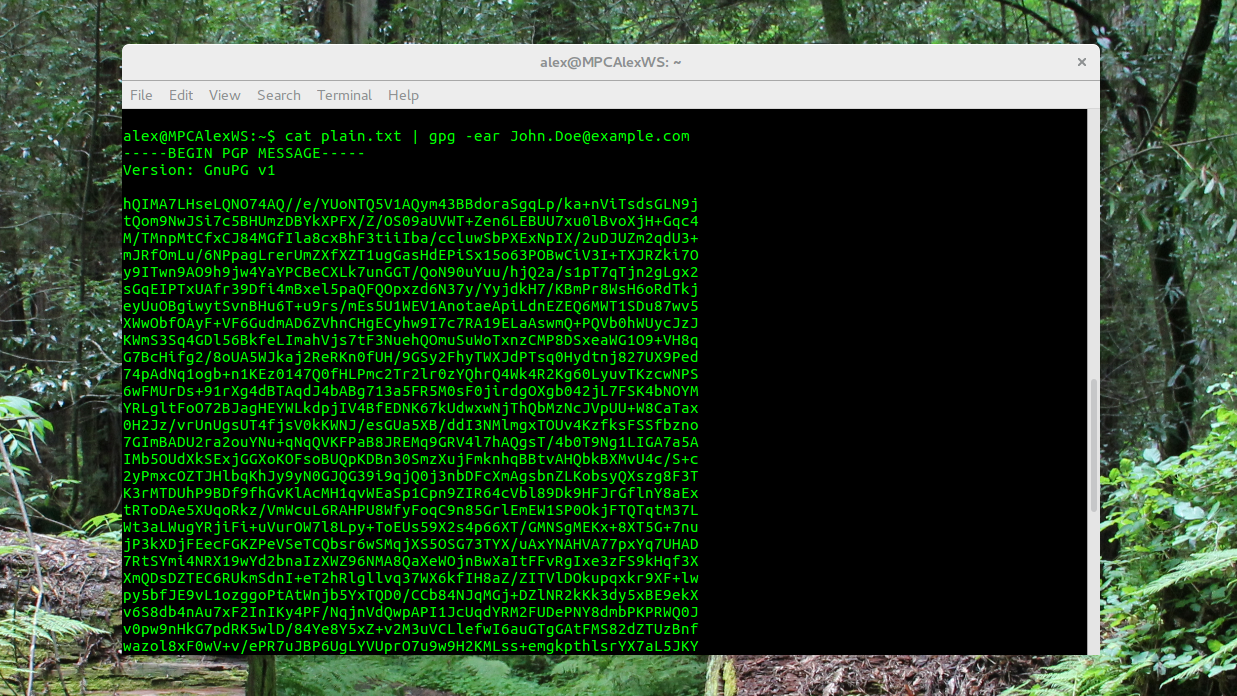
You and I use encryption when checking our bank accounts, when tweeting, when Googling for directions, and (hopefully) when connecting to Wi-Fi at home or the office. Device encryption protects hard drives in financial institutions and our personal cell phones. Your bill suggested that we break systems like these, which we trust to keep our information safe.
Mandating that encryption providers be able to make clear encrypted data when ordered means they have to build a way to override the technology using secondary means (or at the very least use keys that don’t expire, which is inherently unsafe). Even if the bill does not “mandate” design of software, the fact that a provider must be able to comply with the demands of a judge means that the software must necessarily be designed with these possible demands in mind.
That’s what we call a backdoor, and security experts have long warned about the dangers presented by backdoors and key escrows. It takes an astonishing amount of arrogance or ignorance (or both) to think a backdoor will only be used by those it’s designed for. Backdoors, once created, present an additional attack vector for adversaries of all kinds. That’s not even considering that the mathematics underlying modern encryption prohibit such backdoors if they are to remain secure.
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
Key escrows present risk too, as the government would be tasked with securing the keys to the whole kingdom. Seeing how the Office of Personnel Management was breached (and my service record information is in there, thank you very much), that’s a risk that many American companies or citizens simply won’t accept. How can we trust the government with the encryption keys that protect our communications and commerce if we can’t even trust that the government can keep the Social Security numbers and service records of millions of Americans safe? Trusting the government with these keys would make American government systems an even juicier and more valuable target than they already are. And the question remains: How will the government force people to use such escrow systems when simply not providing the government with a key is trivial?
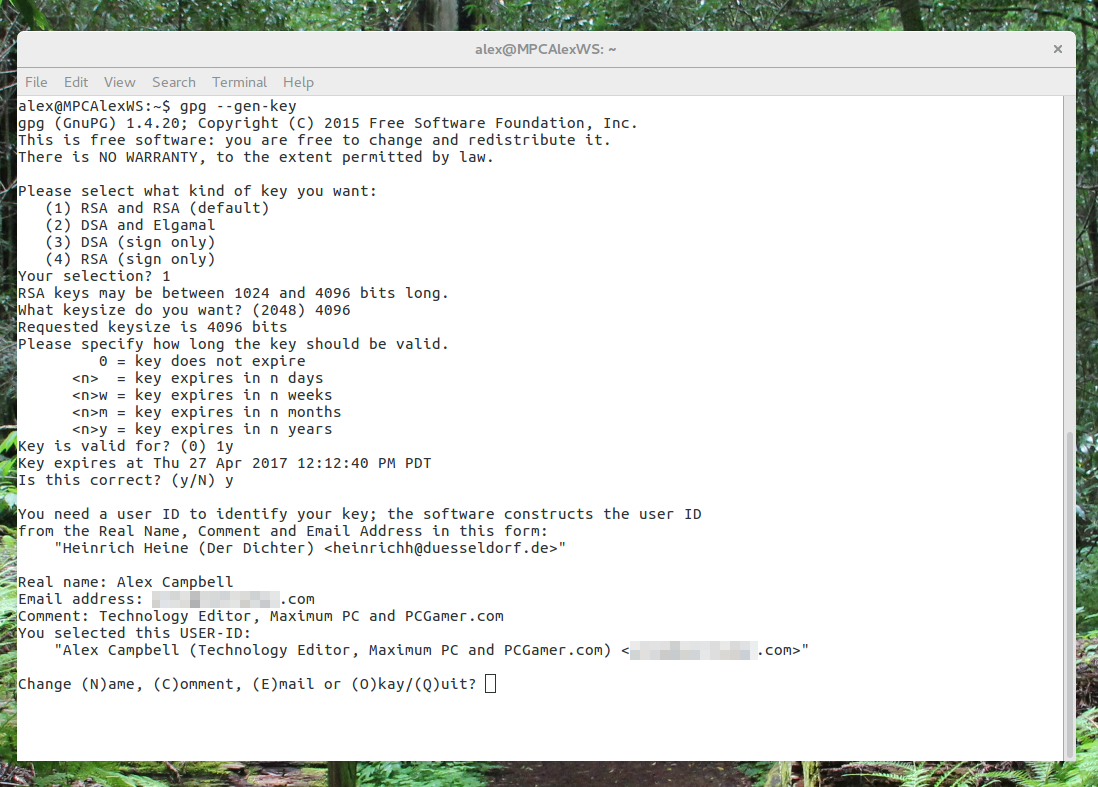
It is absurd to think that by opening backdoors in American encryption that life will be harder on criminals and terrorists. Besides the fact that thinking you're somehow the smartest guy in the room is foolhardy, plenty of foreign companies offer encryption products that may not be covered under US law. Some very strong encryption tools like GnuPG (OpenPGP) and LUKS are open-source. (OpenPGP is often used to encrypt email or digitally sign documents and files proving their authenticity, while LUKS is a disk-encryption scheme that keeps data stored on Linux machines safe from physical theft.) Trying to legislate away source code that anyone has access to is a fool’s errand at best.
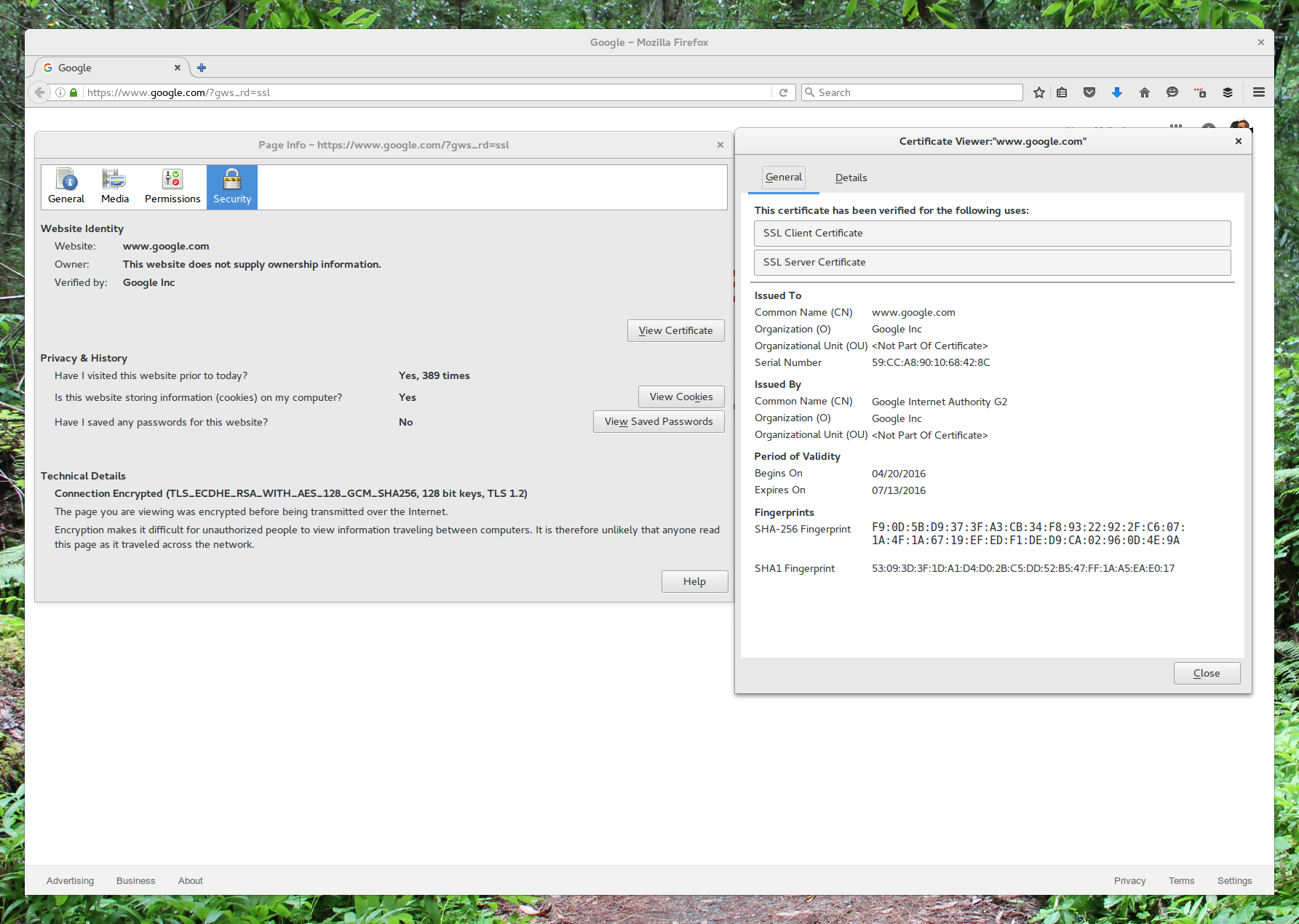
With all of these things in mind, I urge you and your fellow legislators to talk to experts in the field when legislating on this technology. The needs of law enforcement and the intelligence community are not unknown to privacy advocates or the people who spoke at RSA this year. Nearly every RSA speaker agreed that such an attack on encryption endangers the whole Internet (to include America's security interests). Even NSA director Michael Rogers said at RSA that the government and privacy advocates need to talk to one another, not past one another.
Let's make sure that happens before passing brash and uninformed bills.


