Windows 10's built-in antivirus can now be used to download viruses
A recent update to Windows Defender gave it the ability to download files through a command line tool.
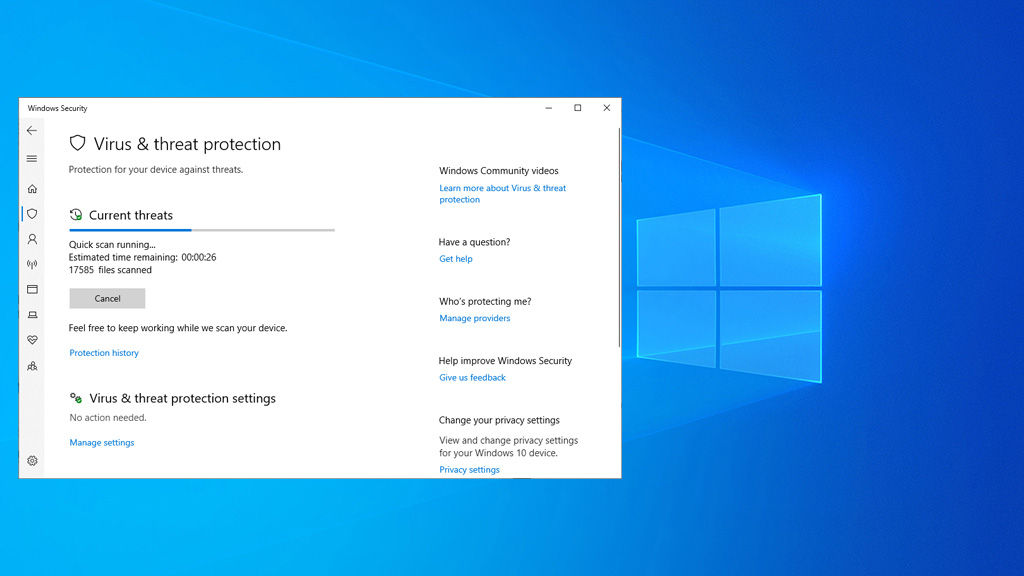
A recent update to the built-in antivirus software in Windows 10 has taught the program a new trick—how to download files through a command line tool, including nefarious ones (trojans, spyware, ransomware, and other malware).
Downloading malware is not the intended purpose, at least I presume that's not the case. But the new function could potentially be abused in such a manner. Fortunately, this is not something the typical home user needs to worry about, not unless they're a PC masochist (more on that in a moment).
This new ability was discovered by Mohammad Askar (via Bleeping Computer), a security penetration tester and instructor who has posted hundreds of security articles, according to his Udemy profile.
"Well, you can download a file from the internet using Windows Defender itself. In this example, I was able to download Cobalt Strike beacon using the binary 'MpCmdRun.exe' which is the 'Microsoft Malware Protection Command Line'," Askar stated on Twitter.
This effectively allows a local attacker to leverage Defender as what is called a living-off-the-land binary (LOLBin). That's when legitimate software is used for something malicious—in this case, using an antivirus program to download a virus.

Best gaming mouse: the top rodents for gaming
Best gaming keyboard: your PC's best friend...
Best gaming headset: don't ignore in-game audio
It appears this new ability was added to Defender with the 4.18.2007.8 update in July, so the functionality has been there for nearly two months. Bleeping Computer tested the new download switch in the command line tool and was able to download the same WastedLocker ransomware that recently caused a ruckus with Garmin's infrastructure, which prompted the company to reportedly pay a multi-million dollar ransom.
This is not quite as careless as it may seem at first glance. For one, Defender will still scan files downloaded through this method, so in theory it should still protect against malware. And secondly, this would need to be initiated by a local user.
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
Nevertheless, this is something system administrators should be aware of, so they can take the proper precautions. It's not unheard of for a rogue employee to cause mischief, whether they are disgruntled, are on the verge of being fired, or any other reason.
Paul has been playing PC games and raking his knuckles on computer hardware since the Commodore 64. He does not have any tattoos, but thinks it would be cool to get one that reads LOAD"*",8,1. In his off time, he rides motorcycles and wrestles alligators (only one of those is true).


