Malware based on Meltdown and Spectre could be coming soon
It's only a matter of time.

For years, there was no attempt to leverage recently disclosed vulnerabilities that exist in a wide range of processors. That's obviously because hardly anyone knew they existed. But now that Spectre and Meltdown are public knowledge, you can expect that to change. The question is, when?
A report at Bleeping Computer points to several instances of security researchers recently finding malware samples based on the newly disclosed security flaws. AV-Test, for example, says it has detected 139 of them, up from 119 samples a week ago.
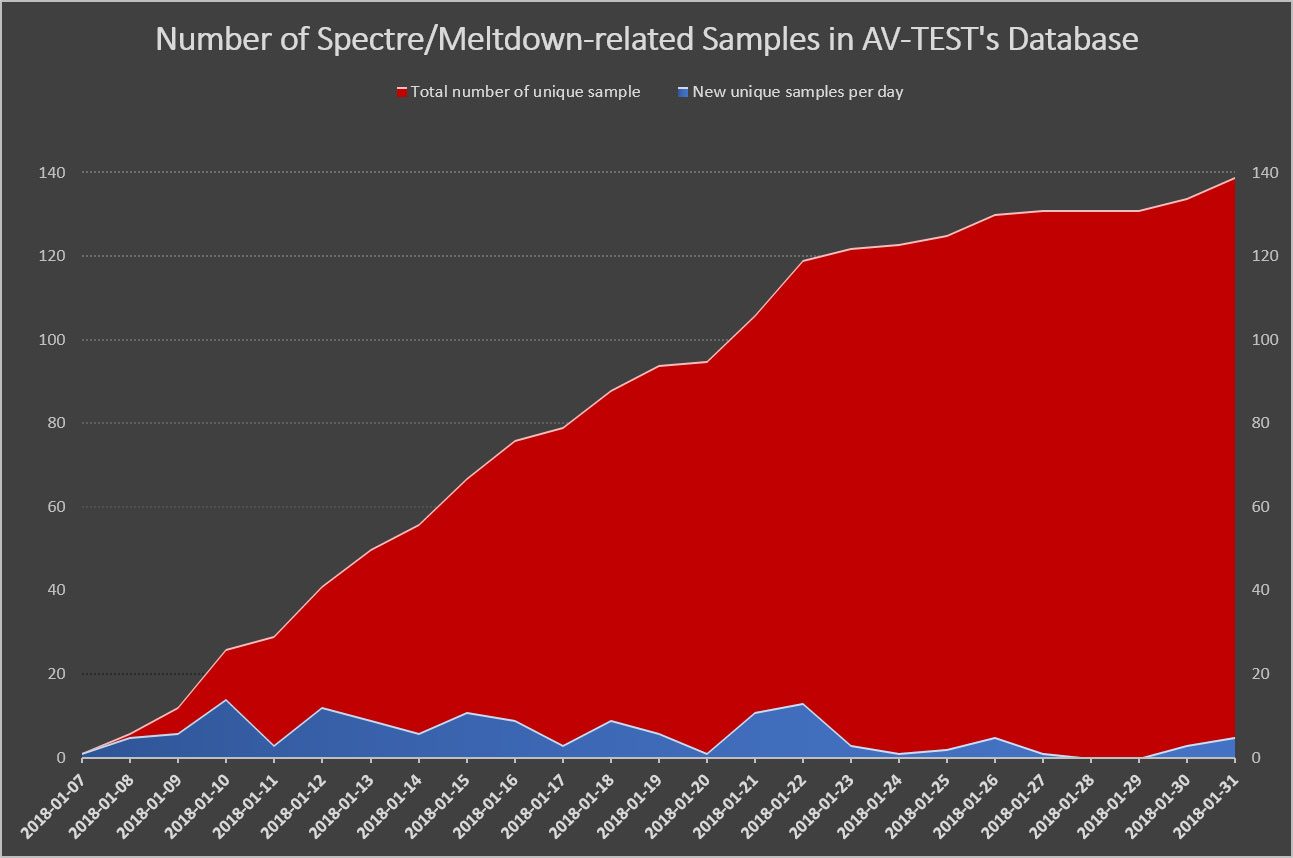
AV-Test plotted out the rise in unique malware detections related to Meltdown and Spectre in a graph, which shows a steep climb over the past month. However, most if not all of them are proof-of-concept samples, most likely developed by the security community at large.
That is the determination by Fortinet, anyway. Fortinet analyzed a large chunk of available malware samples based on Meltdown and Spectre and found they were all experimental in nature.
"FortiGuard Labs has analyzed all of the publicly available samples, representing about 83 percent of all the samples that have been collected, and determined that they were all based on proof of concept code. The other 17 percent may have not been shared publicly because they were either under NDA or were unavailable for reasons unknown to us," Fortinet said.
Playing it safe, Fortinet also updated its antivirus definitions to include protections against the malware samples it analyzed.
Samples have also been detected at VirusTotal. In addition, Mozilla previously confirmed that Spectre can be remotely exploited by embedding malicious code into JavaScrip files on webpages.
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
"Several recently-published research articles have demonstrated a new class of timing attacks (Meltdown and Spectre) that work on modern CPUs. Our internal experiments confirm that it is possible to use similar techniques from Web content to read private information between different origins. The full extent of this class of attack is still under investigation and we are working with security researchers and other browser vendors to fully understand the threat and fixes," Mozilla said at the beginning of January.
So what does all this mean? In short, it means we are probably going to see some real-world attempts at exploiting Meltdown and Spectre sometime in the near future.
Paul has been playing PC games and raking his knuckles on computer hardware since the Commodore 64. He does not have any tattoos, but thinks it would be cool to get one that reads LOAD"*",8,1. In his off time, he rides motorcycles and wrestles alligators (only one of those is true).


