New Intel security flaw affects CPUs as far back as 2008
Researchers say the new MDS attacks are 'worse than Spectre.'

Today, security researchers and Intel revealed a new series of vulnerabilities and exploits called RIDL (Rogue In-flight Data Load), ZombieLoad, and Fallout, collectively classified as MDS attacks, or Microarchitectural Data Sampling attacks. Wired digs into the background in more detail, but early indications are not good. These latest exploits apply similar techniques used in the Meltdown and Spectre vulnerabilities revealed in early 2018, and have the potential to 'leak' otherwise secure data on Intel's CPUs going back at least as far as 2008 models.
How bad are these MDS attacks? Depending on whether you're talking to Intel or the researchers who discovered the techniques, these exploits apparently range in severity from "low to medium" (Intel) to relatively significant—worse than Spectre but not quite as bad as Meltdown. The researches go so far as to suggest it may be necessary to disable Hyper-Threading on Intel CPUs to help thwart these exploits, though Intel disagrees with that recommendation. However, even chips as recent as Intel's latest 9th Gen processors are affected.
All of these vulnerabilities have apparently been 'known' for over a year, but Intel has worked with researchers as well as OS and application companies (including Microsoft, Google, Apple, Amazon, and more) to help get mitigations in place. As with Meltdown and Spectre, the mitigations will generally not hurt performance too much on home PCs, but some datacenter workloads could see performance drop by 8-9 percent.
To put that in perspective, architectural improvements from each generation of Intel CPUs typically only improve performance by about 5 percent, which means a loss of potentially two generations worth of architectural enhancements. And that's apparently on top of the sometimes significant performance loss from the Meltdown and Spectre mitigations.
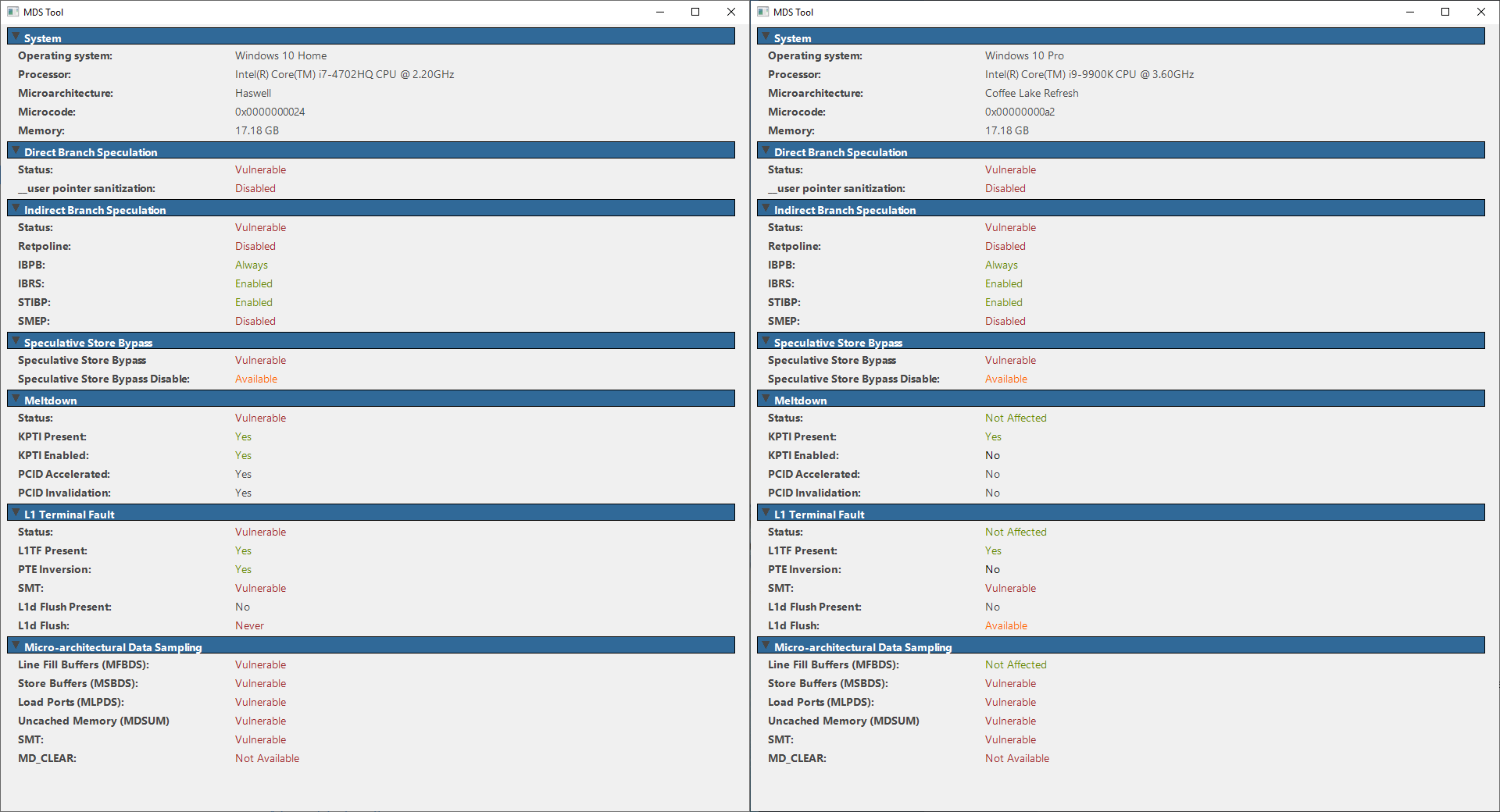
If you want to know if your PC is vulnerable (warning: it probably is), you can download a tool from the MDS attacks site that will provide information on your PC's protected status. (The links are at the bottom, with Windows, Linux, and OSX flavors.) You can see the above capture of data from two of my systems. On the left is my everyday workhorse laptop, a Dell XPS 15 that never received any BIOS or firmware patches with a 4th Gen CPU. On the right is Intel's latest 9th Gen Coffee Lake Refresh, an i9-9900K. It does a bit better, but to my eyes there are still far too many warning signs.
What does this mean for you and your gaming PC? Probably not too much, at least not yet. I'd avoid downloading and running random executables (as a general rule, that's never a good idea), and maybe exercise more caution in what websites you frequent, as theoretically even JavaScript running in a web browser could utilize some of these exploits, but the bigger problems are going to be in cloud services where there's potential to steal data from other virtual hosts running on the same system.
It's worth noting that these MDS attacks do not affect AMD processors. That shouldn't be too surprising, as the attacks rely on knowing and using low level architectural elements of the processor. A completely different architecture (eg, AMD's Zen used in its Ryzen CPUs) would of necessity require a different form of attack. Ryzen systems are safe from these specific MDS vulnerabilities, but that might be because researchers are focusing first on Intel hardware, since it's the dominant solution (particularly for cloud servers).
Keep up to date with the most important stories and the best deals, as picked by the PC Gamer team.
That doesn't mean AMD CPUs are in the clear, however—just as with the original Meltdown and Spectre exploits, this is untamed territory and security researchers expect to discover more variations in the coming months. The list of similar exploits has grown over the past year, including Foreshadow, Spoiler, Lazy FPU Restore, and other side-channel attacks. Still, AMD's latest CPUs so far have managed to avoid coming up as vulnerable in most of the other exploits.
However you slice it, this is yet another red flag in the world of CPUs. If you've been hanging onto an older PC because it's 'fast enough,' upgrading just for the security benefits might start to sound reasonable. Unfortunately, with even 9th Gen Intel being affected at some level (more mitigations are in the works), picking a truly safe CPU might prove difficult. As we said last year, this is clearly not the last we've heard of this sort of attack or exploit.
Jarred's love of computers dates back to the dark ages when his dad brought home a DOS 2.3 PC and he left his C-64 behind. He eventually built his first custom PC in 1990 with a 286 12MHz, only to discover it was already woefully outdated when Wing Commander was released a few months later. He holds a BS in Computer Science from Brigham Young University and has been working as a tech journalist since 2004, writing for AnandTech, Maximum PC, and PC Gamer. From the first S3 Virge '3D decelerators' to today's GPUs, Jarred keeps up with all the latest graphics trends and is the one to ask about game performance.


